Our response to Cloudflare's bug disclosure
Last editedJun 20241 min read
At the end of last week, Cloudflare and Google Project Zero published details of a security issue that affected sites using Cloudflare's web proxy service.
When triggered, the bug led to request data intended for different websites to be mixed together. This meant that a page served by website A could include the contents of a request made to website B.
Because of how widely Cloudflare is used - some measurements put around 5% of the web behind Cloudflare - this is a true internet-scale problem, and warrants a quick response from everyone involved.
As users of Cloudflare's proxy service, we've taken the time necessary to properly assess the risk to our customers and we've done that in partnership with Cloudflare's support team. While the risk to GoCardless data is extremely low, we'd rather be clear with our customers about what's happened.
Our assessment
The risk of data sent to GoCardless having been leaked is extremely low - Cloudflare measured the impact at around 1 in 3,300,000 requests, and there were no instances of requests to GoCardless found amongst the leaked data in web caches.
As we said, we prefer to err on the side of caution when it comes to our customers' data. Based on what we've learned, we've decided to make the following recommendations.
For everyone who logs in to the GoCardless dashboard
We recommend a password change for all users of the GoCardless dashboard. We've written guides on how to do this for users of both our legacy and current dashboards.
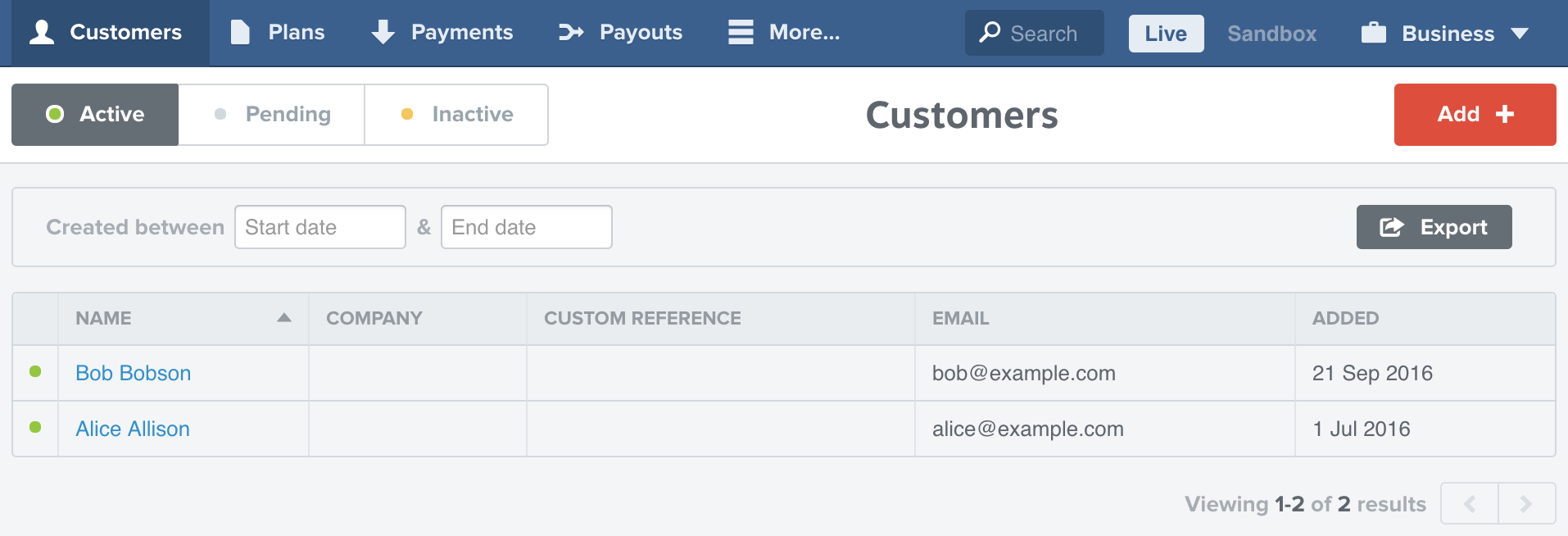
If you're using our legacy product, your dashboard looks like this:
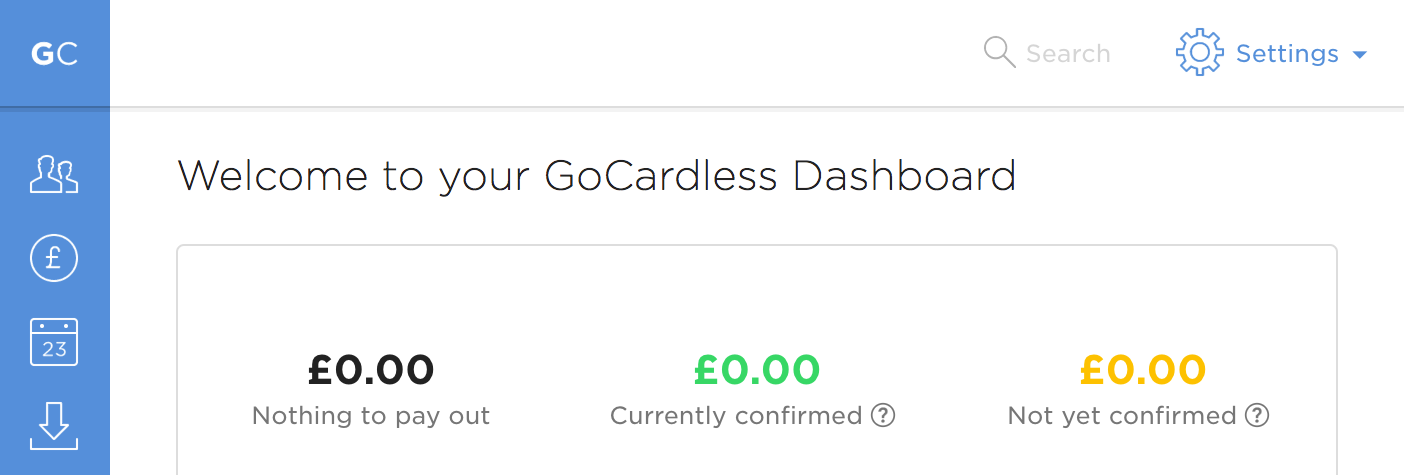
If you're on our current product, it looks like this:
For everyone with an API integration
For API users, we recommend generating new API access tokens and disabling your old ones once your integrations have been switched over. Again, we've written guides on how to rotate your API access tokens for both legacy and current API users.
For everyone who integrates with our Partner (OAuth) product
For partners using our API, if you would like to update your OAuth access tokens please contact support on support@gocardless.com.
Closing thoughts
We know that our customers put a great deal of trust in us when they choose us as a payments provider, and in turn we belive it's fair to provide clarity for them when an issue like this happens.
We hope this post and Cloudflare's own disclosure have all the details you need, but if you'd still like to get in touch with our support team, you can do so by emailing support@gocardless.com.